79 Poplar Street NW Atlanta, GA 30303
Central security services: Protect your company from hackers and viruses
Central Services encompasses many areas of your business that are vital to its continued operation, namely, security concerns and efficiency. Everything from staying up to date on antivirus software to maintaining your backup and disaster recovery measures is necessary to keep your business safe from hackers and ready to spring into action should a problem appear. Monitoring your systems also alerts you to any roadblocks impeding efficiency.
We offer a wide array of remote maintenance and network monitoring services to Atlanta SMBs. These services are all part of our managed IT plans that help us align technology with the needs of SMBs. Growth is often a primary goal for these organizations, and technology alignment allows you to keep pace with the big guys. Central Services is just one piece of the puzzle, but a very important one.
[spacer height=”20px”]
The Goal of our IT Central Services
You need Central Services to keep your environment running and protected. This department, or function in some instances, is accountable for the deployment and management of tools like: Backup and disaster recovery, antivirus, patching, monitoring, content filtering and vendor management.
When considering your Central Services, there are a few things that stand out as primary concerns:
Complete coverage
Unobtrusive
Affordable
Let’s review each of these three aspects and how WorldWide IT addresses them.
Complete Coverage protects your business from hackers
We understand human error is unavoidable, but we can certainly plan for it and do everything we can to counteract it. In addition to accounting for errors, we also need to defend businesses against the possibility of data breaches. Many SMBs make the mistake of thinking they are too small to hack, but a little over a quarter of data breach victims are small businesses, and the results are especially damaging to these organizations. The effects of poor security measures could result in substantial trouble for the future.
The more important the purpose of a tool is, the more stringent the plan must be to protect it.
We have three levels of criticality:
1. It’s important to protect your environment from viruses
Antivirus, antispam, security training, crypto prevent, content filtering, remote access and other tools are all important to daily operations and security. We have two departments that audit them following our documented procedures in SweetProcess:
- Our System Analysts deeply inspect and ensure all tools are set up to meet our standard on a monthly basis.
- Our Technology Officers audit your setup on a quarterly basis.
2. Critical monitoring helps identify hackers quickly
Critical elements include patching and monitoring. Patching is critical in reducing security and productivity loss risks, while proactive monitoring is critical in identifying issues before they negatively impact you and your staff. We have three departments that audit patching and monitoring following our documented procedures in SweetProcess:
- Our System Analysts deeply inspect and ensure the two are set up to our standard on a monthly basis.
- Our Technology Officers audit your setup on a quarterly basis.
- Our Security Manager audits patching and monitoring once a week across 100% of our clients.
When it comes to keeping an eye on things, we offer proactive network and device monitoring throughout Atlanta and the surrounding areas.
3. Mission Critical: be prepared when/if the worst happens
Mission-critical aspects include backup and disaster recovery. They are the most critical as they are the last layer of defense when all else fails. We have three departments that audit backup and disaster recovery following our documented procedures in SweetProcess:
- Our System Analysts thoroughly inspect these aspects and make sure they meet our standards each month. They also perform a quarterly disaster recovery test to simulate a disaster and validate you can recover from it.
- Our Technology Officers audit your setup every quarter.
- Our Security Manager audits backup and disaster recovery for compliance twice a week for all of our clients.
All of WorldWide IT reviews the results of backup and disaster recovery compliance audits across all our clients on a weekly basis:
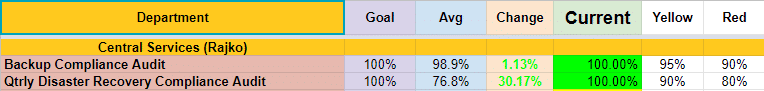
When we detect failures from our audits, we learn from them by performing an ISO 9001-level incident report and consider all issues to be process issues. Growth is the name of the game at WorldWide IT, and we take careful measures to understand how and why any issues occur and prevent them from happening again.
IT Services shouldn’t disrupt your workday
If managing one of your business-critical tools would be disruptive or distracting to your staff, we can always do the work after hours. There’s no point in having them be interrupted by these tasks when we have three live shifts operating 24/7/365. Our staff is always available to work when it won’t impact your productivity.
We also take care to employ tools that won’t negatively impact your systems. For instance, if we install a new antivirus program, your staff probably won’t even notice. We won’t slow down your computers with unnecessary or troublesome programming that could reduce productivity.
One exception to being invisible is our security training. We perform the most advanced simulated phishing attacks randomly twice a month on you and your staff. It takes a few seconds a month and, potentially, an extra 15 minutes of security training when a test is failed. We find that this small time commitment is well worth the significant reduction of risk it provides to protect your business from hackers successfully compromising you and your staff.
Affordable IT Services
We include all of the central services as part of our service fees. This allows us to purchase licenses from tool vendors in bulk and leaves us accountable for the cost as it impacts our bottom line. This means that the more problems you have, the less profitable we are, making positive results a win-win for both of us.
Remote Network Monitoring and Management Services
For proactive network and device monitoring services, WorldWide IT has the skilled staff and managed IT resources to help. We take many steps to ensure safe and secure environments for our clients with our full-coverage, discrete and affordable proactive network monitoring.